2FA is one of the best ways to secure your accounts. But there is a way for criminals to bypass this. Let’s learn how they do it, and how to stop them.
What Is 2FA?
In this article I explain what 2FA “2 Factor Authentication” is, but in brief, it is a way for a website or app to verify that it is really you, not someone else, attempting to sign in. With 2FA, the app or website sends a code to your phone for you to type in.
2FA is pretty secure, but there is a way for criminals to bypass this and get into your accounts.

TOZO T10 Wireless Bluetooth Earbuds
The Tech Boomer recommends these wireless bluetooth earbuds. Clear, crisp sound—plus they’re easy on the wallet!
View on Amazon →This post may contain affiliate links. As an Amazon Associate, I earn from qualifying purchases.
Let’s look at a scenario:
- You get a text from your bank telling you that there is something wrong with your account.
- It looks legit, as it comes from the same number that you usually get bank notifications from.
- The text has a link to your bank “www.your-bank.com” and instructs you to click on it.
- You are then taken to your bank’s website where you are prompted to enter your username and password.
- Since you have 2FA set up, you then receive a text from your bank with a code to enter into the site to verify that it is you. After all, you should be the only one with your phone.
- You enter the code, and then you are taken to another site where you are told that your account looks ok.
You have just been robbed!
but what about 2FA?
Lets look at each of these steps. What the perception is, and what the reality is:
Perception: You get a text from your bank telling you that there is something wrong with your account.
Reality: The text wasn’t from your bank, but from some crook.
Perception: It looks legit, as it comes from the same number that you usually get bank notifications from.
Reality: Phone numbers can be easily spoofed.
Perception: The text has a link to your bank “www.your-bank.com” and instructs you to click on it.
Reality: The link might say www.your-bank.com, but actually it goes to a site the crook has set up.
Perception: You are then taken to your bank’s website where you are prompted to enter your username and password.
Reality: It’s not your bank’s website. Someone has made a copy of it. Very easy to do. When you enter your username and password, it is captured by the fake site. They then use it to log into your real bank’s site. This is usually done through automation.
(Here’s a BBB article to help you spot a fake website).
Perception: Since you have 2FA set up, you then receive a text from your bank with a code to enter into the site to verify that it is you. After all, you should be the only one with your phone.
Reality: This is real. When the bad guys attempt to sign into your bank, the bank sends you the code.
Perception: You enter the code, and then you are taken to another site where you are told that your account looks ok.
Reality: You just entered the code into the fake site, and the crooks in turn entered it into the real site. Now they are logged into your bank.
Scary, isn’t it? This is called “advanced adversary-in-the-middle phishing attacks (AiTM).”
How do you combat AiTM?
There is only one way. Don’t click on links in texts or emails. Period.
Open the app, or use your browser to go to the site in question.
Recently, I received a text from my bank:
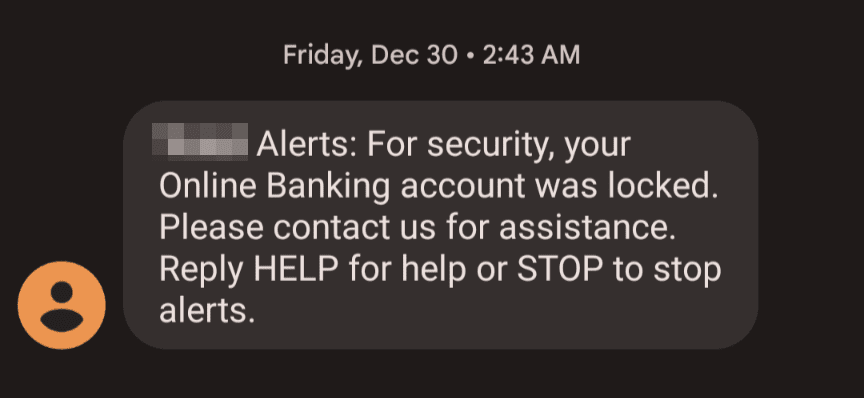
It didn’t have a link or phone number to call. I went to my computer and attempted to sign in to my bank and found that I was locked out. I had to reset my password to get in. It turns out that someone had my user name and was trying to guess my password. They got locked out after too many tries.
The next day I received the same message. This time I changed my username as well. Hasn’t happened since.
This is an example of how a bank (or any other service) should handle this.
While 2FA is safe when used properly, it is ultimately up to us to make sure it is used properly.
As always, if you have a question about this or any other post, please leave a comment below, or you can email me at larry@thetechboomer.com.

OTC Hearing Aids for Seniors
OTC Hearing Aids for Seniors, Hearing Aid Amplifiers Devices Rechargeable with Noise Cancelling, Superior Sound Quality for Adults Women Men Hearing Loss, Auto On/Off
View on Amazon →This post may contain affiliate links. As an Amazon Associate, I earn from qualifying purchases.




